by Kelvin Wong | Photo credits: securityaffairs.co, post852.com | 14 November 2014
On 22 June 2014, the HKU Public Opinion Programme (HKUPOP) website suffered from a massive Distributed Denial of Service (DDoS) attack during the voting for civil referendum. The scale of the attack was considered to be the second largest DDoS attack in internet history. DDoS attack can bring down mainframe computers and website servers, and it is an issue everyone should pay attention to because you may unintentionally become one of the contributors to these attacks.
How DDoS works
DDoS attack is based on a fundamental concept – if a computer wants to browse a webpage, the server will respond to them and send the computer the relevant webpage. If there are too many computers requesting the server to send information, the server may not have the capacity to handle a large number of requests and its efficiency may be lowered as a result. This can be done by pinging the website server very frequently in a very short period of time.
However, a single computer cannot generate requests on a scale so large that can slow down the server. Also, the network bandwidth may constrain the effectiveness of the attack. Therefore, some hackers have thought of a solution – what if many computers connect to the same server at the same time?
Some developers put their software online and allow net users to download freely. The software is sometimes bundled with Trojan horse. Once the software gets installed, the computer will follow any ping server request made by the developer and carry it out automatically without user’s consent. If many computers have installed the Trojan horse that connects them to the target server again and again, the server can definitely be slowed down. However, these consecutive ping requests can slow down the processing speed of these ‘zombie computers’, which is an infection issue that remains widely discussed in the computer world.
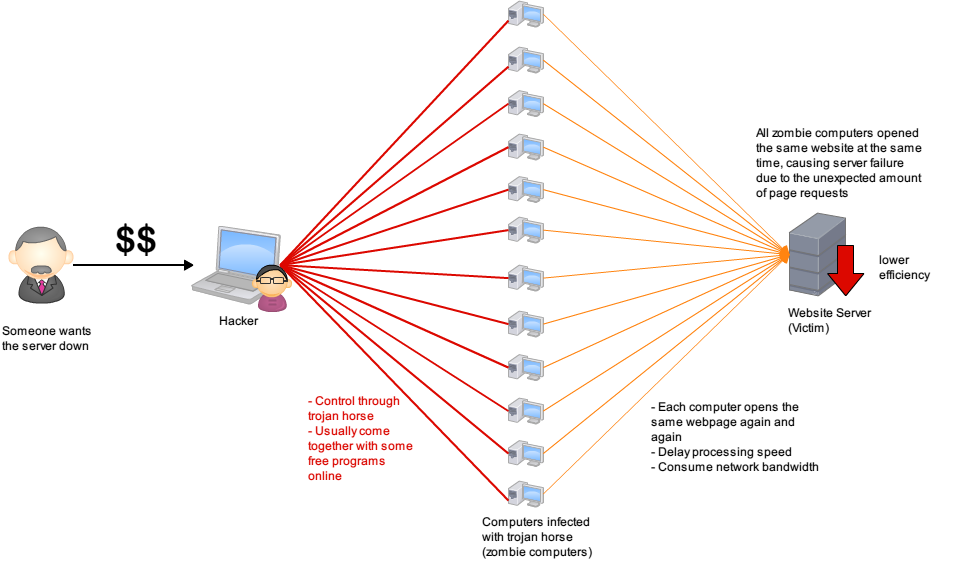
Free online software is often bundled with malicious scripts. If these scripts are installed by users, the computer may become a member of the zombie networks, which can be controlled by hacker to launch attack against target servers. High-frequency attack can greatly reduce processing speed of computers and put burden on network bandwidth.
Actual implementations of DDoS
For IT hackers…
DDoS can be implemented in various ways. One of the most common ways is Syn attack, in which a client opens TCP connection without closing it. The action of handshake is never finished, hanging the server to pend for webpage requests. Another method is to use an open DNS resolver, craft a fake UDP packet with the anonymous address and send it to the server. The server may send back webpage package data to the IP address which does not exist (or the one not making the request). This can also contribute to a decrease in server processing speed.
For website administrators…
Server administrators can take some preventive measures to minimize the possibility of DDoS attack against their own servers. For example, the server should always find a redundant DNS server by registering two or more DNS server addresses. Their connection ports should also be blocked except those that are really in use. An efficient load balancing strategy can promote the speed of handling each request received. A content delivery network should be established to deliver packages to its clients in a distributed manner. Routers can learn to drop large amount of junk packets. It is important to protect your server from Syn attack with the aid of TCP backlog or Syn cache. In fact, caching servers can store static content which reduces internal processing.
To further protect our server from DDoS attack, website administrators can subscribe to a secure server host for their websites. Currently some website host providers offer security protection against DDoS attack with their rich experience in dealing with certain attacks. Cloudflare, for example, is the only server provider that maintains the service of HKU POPVote website in June 2014 when the other two subscribed web host providers (one of which is stored in Amazon Web Services) were down. Therefore, choosing a secure and stable web host is important for building durable websites.
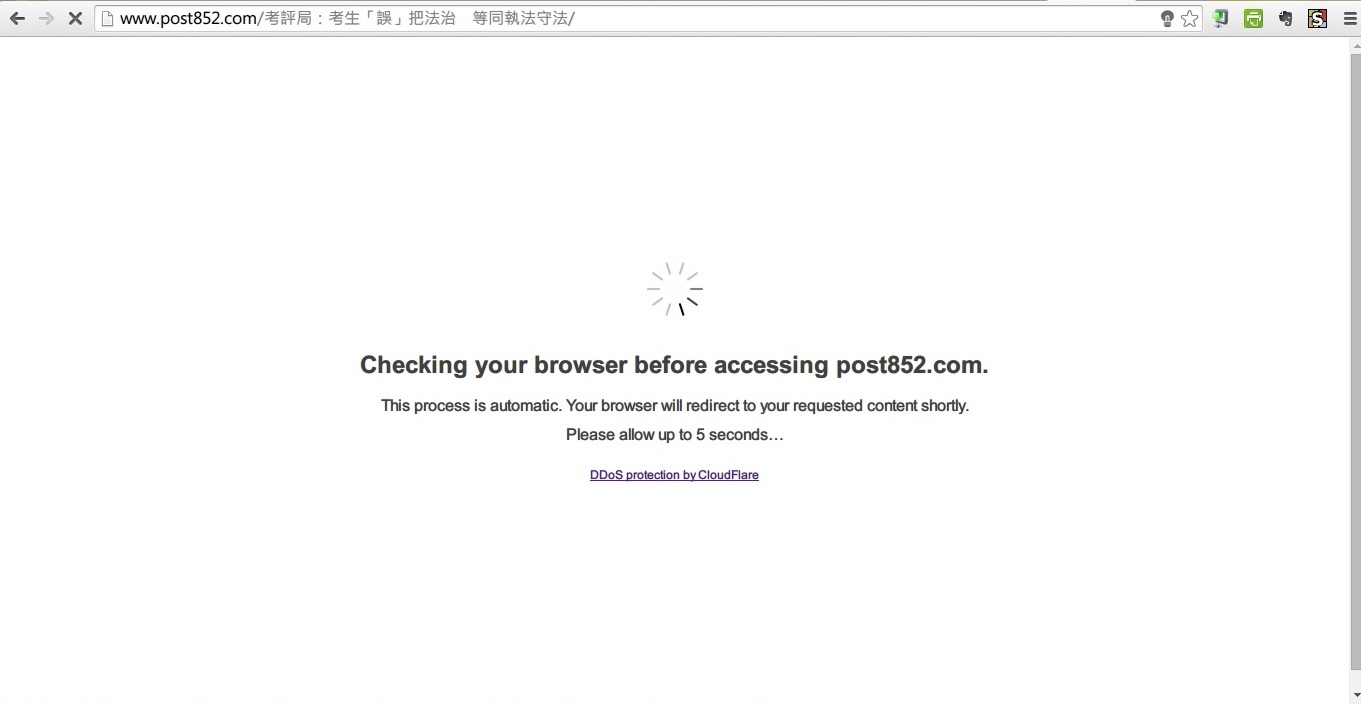
Some website host providers offer DDoS protection to further secure websites from anonymous DDoS attack.
For users…
This may sound corny, but it is worth reminding our users again not to install any free software by unknown publishers online. They may contain some malicious script that can turn your computer into a member of zombie networks, contributing to DDoS attack and significantly affecting the processing speed of your own computer. Scan your computer regularly using anti-virus and anti-malware software to keep your computer clean. Set up a firewall and block ports (if possible) to limit the access of unknown terminals.
Kelvin Wong
Latest posts by Kelvin Wong (see all)
- Poor pitching skills and low exposure may be blunting local students’ competitive edge: FYP Tips - July 8, 2015
- Uber — Helping or Exploiting Taxi Drivers? - February 13, 2015
- How to Deal with DDoS Attacks - November 14, 2014